Data
protection
Useful information to help you understand how we protect your personal data.
Global data protection policy
Published on 20 December 2024
1. Scope
Everyone has rights with regard to how their personal information is handled, and Iress recognises that the lawful and correct treatment of personal information is vital to our continued success in an increasingly regulated global marketplace. “Personal information” (which is generally considered as any information which is capable of identifying a living individual [1]) is collected, received and processed every day in our business. During the course of our activities we process personal information about our staff, contractors, suppliers, clients and our client’s customers (collectively, ‘data subjects’); and we are committed to ensuring that it is treated in an appropriate and lawful manner.
Iress Limited is our parent company based in Australia, we also have operations in several other countries, including the United Kingdom, France, South Africa, Canada, New Zealand, and Singapore. This document does not set out a detailed explanation of the data protection legislation in each country in which we operate, but its aim is to establish a uniform minimum standard which applies to all processing of personal information that we carry out. In addition, where we engage subcontractors, consultants, suppliers and business partners who handle personal information on our behalf, we expect these third parties (irrespective of where they are based) to have in place appropriate policies, procedures and technical/organisational measures which provide an equivalent level of protection in relation to the processing of personal information as those set out in this document.
2. When does this policy apply?
This policy applies when we are processing personal information; this may be information which Iress has collected directly from a data subject or where we have received it from a third party such as the clients who we provide software and services to.
What is personal information?
For the purpose of this policy, personal information is information which relates to living individuals [2] who can be identified directly from that information, or indirectly through its combination with other information we hold, or are likely to have access to.
Personal information can include a wide variety of information, such as names, addresses (physical or email), telephone numbers, an identification number, location data, online identifiers and financial information. It can also include an opinion about an individual, their actions and behaviour. Personal information which is more sensitive [3], could include details about a person’s health or genetics, racial or ethnic origin, sexual orientation or gender identity, marital status, political opinions, religious beliefs and criminal background [4]. We will identify where personal information being processed is sensitive as this may impact on our purpose for processing that information, as well as the technical and operational measures we need to adopt to ensure the information is appropriately protected.
Personal information may be processed by Iress in electronic or hard copy form.
What is processing?
The definition of processing is very wide. Activities such as obtaining, collecting, receiving, storing, recording, holding, using, disclosing, updating, hosting, analysing, viewing, accessing, making available, copying, transferring, anonymising or deleting personal information can be considered “processing”.
3. Collection of personal information
In cases where we collect personal information directly or indirectly from data subjects and we determine the manner and purpose for which it is processed, then we ensure that we are open and transparent with data subjects by providing them with certain information regarding how we use their personal information - this is usually in the form of a specific privacy (collection) notice and/or privacy policy.
The specific information to be included in a privacy notice or policy can vary depending on where our operations are located, and/or where the data subject is located, and may also vary depending on whether we collect the personal information directly from the data subject or we obtain it from a third party. Our main privacy notices and policies can be accessed from https://www.iress.com/resources/legal/privacy/, where regional specific privacy notices and policies are available.
In cases where we process personal information in connection with the services we provide to our clients, we generally rely on our clients to ensure that they provide all required information to data subjects (including customers of our clients) which is sufficient in scope to enable us (and, if relevant, any third party providers who provide services to that client on behalf of Iress) to process the personal information in the course of the provision of our services. In some circumstances, and in certain jurisdictions in which we operate, it may be necessary for our clients to obtain the explicit consent of the data subject in order for Iress to process the data subject’s personal information. In these circumstances we will rely on our clients to ensure that such consents are in place prior to sharing personal information with us.
4. Global data protection principles
In certain countries in which we operate, responsibility for compliance with the principles set out below will depend on the specific privacy legislation of that country and the capacity in which Iress acts. For example, in the United Kingdom not all of these principles may apply if we are acting only as a processor of personal information on behalf of an Iress client.
a) Personal information must be processed fairly and lawfully - for personal information to be processed lawfully, certain conditions have to be met. Whilst a common way of establishing compliance with this principle may be to obtain the consent of the data subject to the processing [5], there may be a more appropriate basis upon which we can rely to show that we are processing information fairly and lawfully. The legal basis to support lawful processing can vary dependent on jurisdiction – examples include where the processing satisfies a legal obligation (as opposed to a contractual obligation), where the processing is necessary to enter into or carry out a contract to which the data subject is party (for example to process a job application or to administer employee pensions or payroll) or where the processing is necessary for the purposes of the legitimate interests pursued by Iress (except where those interests are overridden by the interests, rights or freedoms of the data subject).
Where we are carrying out processing activities on behalf of our clients we will generally rely on our clients collection of personal information, and their provision of any relevant personal information to us, being in compliance with the fair and lawful processing principle and any relevant regional privacy legislation [6].
b) Personal information must be processed for limited specified purposes - personal information may only be processed for the specific purposes notified to the data subject, for a (secondary) purpose which is compatible with that specific primary purpose, or for any other purposes permitted by legislation. This means that Iress will not collect personal information for one purpose and then use it for another unconnected purpose, unless we are legally or contractually entitled to do so. If it becomes necessary to change the purpose for which the information is processed, beyond the purpose notified to you, we will inform the data subject of the new purpose. In addition, (depending on how the new purpose relates to the initial purpose in terms of compatibility), it may be necessary to obtain the data subject’s prior consent before starting processing under the new purpose [7].
Where we are processing personal information in connection with services provided to our clients we do so only in accordance with the purposes we have agreed with that client – whether in our contract with that client or in response to a clients’ express instructions.
c) Personal information must be adequate, relevant and limited to what is necessary in relation to the purposes for which it is processed – in circumstances where we collect personal information we will consider what is necessary to collect in light of the purpose(s) of the processing limiting the collection to data which is necessary to that processing activity.
d) Personal information must be kept accurate and, where necessary, up to date – where we are collecting personal information reasonable steps will be taken to check the accuracy of any personal information at the point of collection and at regular intervals afterwards. Every reasonable step should be taken to ensure that personal information that is inaccurate or out-of-date is rectified or destroyed without delay, unless it has been agreed with the Privacy Adviser that there is a legitimate purpose for retaining this personal information, such as for record-keeping purposes.
Where we are processing personal information on behalf of our clients we will ensure that we have appropriate processes or functionality in place in our system to enable inaccurate data to be rectified.
e) Personal information must not be kept for longer than is necessary – personal information must not be kept in a form which permits identification of data subjects for longer than is necessary for the purposes for which the information is collected and processed. Personal information will be destroyed, anonymised or erased from our systems when it is no longer required, unless there is a legitimate reason to retain it.
Retention decisions may be based upon our legal obligations to retain personal information and/or documents for specified time periods or contractual obligations owed to our clients [8]. We may also need to retain certain personal information beyond our normal retention periods where this is based on our legitimate interests or a specific legal obligation, for example when we need to keep information to defend future legal claims.
f) Personal information must be processed in line with the data subject’s rights - dependent on the jurisdiction in which the data subject is resident, data subjects generally have a right to:
a) be informed about the collection, use and disclosure of their personal information;
b) request access to any personal information held about them (see paragraph 8 below – Dealing with Subject Access Requests);
c) ask to have inaccurate personal information amended, or to have any incomplete or out-of-date personal information updated;
d) object to, or prevent, the processing of their personal information on reasonable grounds, including where the processing is likely to cause them harm (damage or distress);
e) object to the processing for direct marketing purposes at any time;
f) request the restriction of processing in certain circumstances;
g) request that personal information is deleted without undue delay [9];
h) lodge a complaint with a supervisory authority.
In certain countries in which we operate, data subjects have additional rights, including: (i) the right to obtain from Iress a copy of all personal information which the data subject has provided to the controller in a structured, electronic format that is commonly used and which permits further use by the data subject (known as data portability); (ii) the right not to be subject to automated decision making, including profiling; (iii) the right not to have personal information processed for the purposes of direct marketing by means of unsolicited electronic communications and (iv) the right to initiate legal proceedings against Iress if we have breached relevant privacy legislation.
Where we are processing personal information on behalf of our clients we will ensure that our systems and processes enable us to assist our clients in responding to requests made by data subjects exercising their rights.
g) Personal information must be kept secure - appropriate technical and organisational measures are put in place to protect personal information against unlawful or unauthorised processing of personal information, and against the accidental misuse, unauthorised access to, loss of, or damage to, personal information. Procedures and technologies are in place to maintain the security of all personal information from the point of collection to the point of destruction. Maintaining data security in this manner ensures the confidentiality, integrity and availability of the personal information.
For more information on the steps we take to ensure the security of personal information we process please refer to our information security policy.
h) Personal information should be transferred to third parties with caution – we will be transparent in relation to any transfers of personal information through our relevant privacy notices and/ privacy policies. In certain jurisdictions in which we operate we must ensure that we do not transfer personal information to a third party unless the data subject has consented to such transfer, or both the recipient and the recipient country have adequate privacy protections in place that are comparable to our own (as further noted below).
Where we are processing personal information on behalf of our clients, any transfers will be made in accordance with our contractual commitments, as well as any relevant privacy legislation. Whenever we are transferring data to our sub-processors, care is taken to ensure that any recipient treats information transferred to it appropriately – this is usually achieved through due diligence and a written agreement between Iress and the other party (see paragraph 6 below).
i) Personal information can only be transferred by Iress outside of the country in which it is collected in certain circumstances – as Iress is a global organisation this principle is particularly important to our business – our approach to cross-border transfers is therefore detailed in paragraph 7 below.
5. Data Protection Impact Assessments/ Privacy Impact Assessments
To support the appropriate handling of personal information, Iress understands the importance of privacy by design and default; we consider privacy and data protection issues as we design our software and services, and throughout our processing activity.
Before commencing any processing which is likely to result in a risk to data subjects, when engaging a third party who will process personal information on our behalf, and when implementing major system or business change programs involving the processing of personal information(for example, new technologies, programs, systems or processes), Iress will review the envisaged processing to assess the privacy risks, and identify measures to address these risks and demonstrate compliance with the privacy legislation in the relevant jurisdiction [10]. Relevant considerations will be documented in a Data Protection Impact Assessment (DPIA) with the EMEA region or a Privacy Impact Assessment (PIA) within APAC; in global initiatives a hybrid assessment will occur.
6. Appointment of another party to process personal information on Iress’ behalf [11]
Where we appoint another party to process personal information on our behalf then we will put in place a contract with that other party which imposes certain obligations on them, including obligations to comply with security requirements, to process personal information only in accordance with our instructions and not to engage further sub-processors without Iress’ consent. Iress has a procurement process which will support the onboarding of suppliers and requires engagement with the legal and privacy team to support contractual review and a relevant DPIA and/or PIA if appropriate.
7. Cross-border transfers
Transfer or Transit?
Any action that allows personal information to be accessed or makes the personal information available, or potentially available, to someone outside of the country in which the information was collected could amount to a ‘transfer’ of that personal information.
A transfer will not be deemed to have occurred if the personal information simply passes through another country on the way to a final destination unless some processing takes place in the other country en-route. In the context of the electronic transmission of personal information, this means that even though information may be routed through a third country on its journey from one country to another, this mere transit through a third country/ countries does not bring the transfer within the scope of the privacy legislation [12].
Can information be transferred outside of the country in which it was collected?
The rules in each jurisdiction are different, and a brief summary is below. Iress will ensure that suitable transfer mechanisms are in place for all international transfers of personal information.
United Kingdom and France
Personal information may be transferred outside of the UK or the European Economic Area (EEA) if any one of the following conditions are met:
a) the UK Government/ European Commission has made a finding of adequacy in relation to the country to which the personal information is being transferred (note that findings have been made, for the UK, Canada and New Zealand - which are countries in which Iress is located [13]);
b) when the transfer of personal information is covered by certain standard clauses approved by the European Commission or the UK Information Commissioner’s Office (ICO);
c) the data subject consents explicitly to the transfer, after having been informed of the possible risks of such a transfer due to the absence of an adequacy decision and appropriate safeguards;
d) the transfer is necessary for the performance of a contract between the data subject and Iress, and the transfer is occasional (the transfer may happen more than once, but not regularly);
e) the transfer is necessary for the conclusion of performance of a contract concluded in the interest of the data subject between Iress and another individual or company, and the transfer is occasional (the transfer may happen more than once, but not regularly).
Where the condition in (b) is relied upon, the transfer may only be carried if the parties involved in the transfer have provided appropriate safeguards and on condition that enforceable data subject rights and effective legal remedies for data subjects are available in the country outside of the EEA or UK (as applicable). Iress will undertake a transfer risk or impact assessment for international transfers where an adequacy decision is not held by the receiving country. Suppliers of Iress are required to ensure personal information is processed in accordance with relevant privacy legislation including the laws relating to international transfers.
Australia
As a general rule, personal information may be transferred to an overseas recipient where the entity disclosing personal information takes reasonable steps to ensure that the recipient does not breach the Australian Privacy Principles (APPs) and Iress will remain accountable for any breaches of the APPs. However, such reasonable steps are not required in any of the following situations:
a) the recipient of the personal information is subject to laws which offer a level of data protection substantially similar to the APPs and the data subject has access to mechanisms to take action to enforce the protection of those laws;
b)the individual consents to the transfer (noting that the organisation must, prior to receiving such consent, expressly inform the individual that if they consent to the overseas disclosure of the information, the organisation will not be required to take reasonable steps to ensure the overseas recipient does not breach the APPs);
c) a "permitted general situation" exists (this includes circumstances where disclosure is necessary to prevent a serious threat to life; where an organisation suspects unlawful activity or serious misconduct; for locating an individual reported as missing; or where disclosure is necessary to establish or defend a legal or equitable claim);
d) the disclosure is required or authorised by law or a court/tribunal order.
South Africa
Personal information may be transferred to an overseas recipient where at least one of the following applies:
a) the recipient of the personal information is subject to a legislation or contract which provides for an adequate level of protection which is substantially similar to the level of protection offered under the Protection of Personal Information Act (PoPI);
b) the data subject consents to the transfer;
c) the transfer is necessary for the performance of a contract, or for the implementation of pre-contractual measures at the data subject’s request;
d) the transfer is necessary for the conclusion or performance of a contract concluded in the interest of the data subject between the responsible party and a third party; or
e) the transfer is for the benefit of the data subject and it is not reasonably practicable to obtain the data subject’s consent, and if it were reasonably practicable to obtain such consent, the data subject would be likely to give it.
Canada
The federal private sector privacy legislation (the Personal Information Protection and Electronic Documents Act 2000 (“PIPEDA”)) does not prohibit organisations from transferring personal information outside of Canada. However, the transferring entity is accountable under the privacy legislation, and is expected to use contractual means to ensure a comparable level of protection of the personal information.
Singapore
As per the Personal Data Protection Regulations 2021, Iress may transfer personal data overseas where we have taken appropriate steps to ensure that the overseas recipient is bound by legally enforceable obligations or specified certifications to provide the transferred personal data a standard of protection that is comparable to that under the Personal Data Protection Act 2012 (PDPA).
Mechanisms to achieve a comparable level of protection may include: data transfer agreements (which the Singapore Personal Data Protection Commission has released - including model clauses); the individual has given consent (with prior notices in place); where transfers are considered necessary in certain circumstances (which include in connection with performance of contracts between the transferring organisation and the individual, subject to certain conditions being met).
New Zealand
Transfer of personal information outside of New Zealand is permitted provided that the country to which the data is transferred provides comparable safeguards to New Zealand privacy legislation or the receiving organisation agrees to protect the information to the same standards and this is noted in the associated contract or through the use of model contract clauses .
8. Dealing with data subject rights requests
Any individual within Iress may receive a request from a data subject wishing to exercise their data protection rights. Such requests will be shared with the legal / privacy team and/or people team to enable appropriate review and action in accordance with the relevant privacy legislation. Should a request be received related to Iress’ handling of personal data on behalf of an Iress client these will be forwarded promptly to our clients in accordance with our contractual obligations.
9. Implications of non-compliance
The implications of non-compliance with privacy legislation are serious, and range from regulatory enforcement action (which could include significant financial penalties), commercial penalties under our client contracts and reputational damage. In some jurisdictions in which we operate, more serious contraventions could amount to a criminal offence and our directors could be found personally liable.
10. Breach reporting
Any identified breaches of this policy can be reported directly to the privacy team via compliance@iress.com.
We maintain internal policies and procedures to ensure that any data breach (or suspected data breach) is reported promptly and actioned in accordance with legal and contractual requirements.
11. Review of the Policy
We will regularly review this policy and it will be amended from time to time; further details on changes to the policy over time can be seen in the version control details below. Any questions or concerns about the content of this document or how Iress processes personal information, should be referred to the privacy team via compliance@iress.com. Further information about Iress handling of personal information can also be found in our specific privacy notices and privacy policies, and associated privacy information available at https://www.iress.com/resources/legal/privacy/ .
Further details as referenced within the policy:
[1] In South Africa, the Protection of Personal Information Act 2013 (PoPI) gives a ‘juristic person’ (which is defined as a company, entity, community or other legally-recognised operation), the right to the protection of its personal information. This means that our South African operation must also safeguard the information it holds about clients who are companies, as well as business partners, integrators, suppliers etc.
[2] As well as juristic persons in South Africa and in very limited circumstances deceased individuals in Canada and Singapore.
[3] Sensitive personal information is also known as a “special category data’’ under the General Data Protection Regulation (within the UK & EU).
[4] This is not an exhaustive list of what may amount to personal information in each jurisdiction in which we operate. Our legal and privacy teams provide support to the wider business in identifying whether information is included within the scope of this document and how to meet its obligations.
[5] When Iress does rely on consent as the basis of lawful processing, certain rules apply in relation to the manner in which we collect consent based on the location of the data subject. Generally individuals will retain the right to withdraw consent at any time, at which point processing activity will cease, unless a relevant exemption applies.
[6] With Australia, where there is no direct equivalent of the data controller or processor roles, Iress may be required to provide the data subject with additional privacy information in respect to our processing of personal information to satisfy its regulatory obligations.
[7] When deciding whether a purpose is compatible with another, we may consider the nature of the personal information, if there is any relation between the two purposes, what the data subject would reasonably expect from the processing and any possible consequences the new processing might have on the data subject.
[8] For those processing in the UK, South Africa and Australia, please refer to our Data Retention Policy for further guidance on our legal obligations to retain certain documents and guidance on setting retention periods.
[9] There may be grounds for refusing to comply with this type of request – for example, if the data remains necessary in relation to the purpose for which they were collected, if it needs to be retained for legal reasons or where the Iress has an overriding legitimate grounds for the processing.
[10] The approach to privacy related assessments vary by region, but will be generally focused on identifying and considering mitigation of any privacy risks caused by the intended processing of personal information and demonstrating Iress’ approach to complying with relevant privacy law.
[11] Paragraph only applicable to Iress companies in the UK, EU and South Africa.
[12] Case law in the United Kingdom has held that uploading personal information onto a webpage only constitutes a transfer to another country if the relevant webpage is actually accessed by a person located in that country. The process of merely uploading the data does not fall within the scope of the legislation.
[13] The European Commission has recognised Andorra, Argentina, Canada (commercial organisations concerning data subject to PIPEDA), Faroe Islands, Guernsey, Israel, Isle of Man, Japan (private sector organisations), Jersey, New Zealand, Republic of Korea, Switzerland, the UK, the United States of America (under the EU-US Data Privacy Framework and the UK extension) and Uruguay as providing adequate protection. The UK recognises the above countries, with the addition of all EEA and EFTA members and Gibraltar, as having adequate safeguards for the transfer of personal information.
12. Footnotes
Further details as referenced within the policy:
[1] In South Africa, the Protection of Personal Information Act 2013 (PoPI) gives a ‘juristic person’ (which is defined as a company, entity, community, or other legally-recognised operation), the right to the protection of its personal information. This means that our South African operation must also safeguard the information it holds about clients who are companies, as well as business partners, integrators, suppliers, etc.
[2] As well as juristic persons in South Africa and in very limited circumstances deceased individuals in Canada and Singapore.
[3] Sensitive personal information is also known as a “special category data’’ under the General Data Protection Regulation (within the UK & EU).
[4] This is not an exhaustive list of what may amount to personal information in each jurisdiction in which we operate. Our legal and privacy team provides support to the wider business in identifying whether information is included within the scope of this document and how to meet its obligations.
[5] When Iress does rely on consent as the basis of lawful processing, certain rules apply in relation to the manner in which we collect consent based on the location of the data subject. Generally individuals will retain the right to withdraw consent at any time, at which point processing activity will cease, unless a relevant exemption applies.
[6] With Australia, where there is no direct equivalent of the data controller or processor roles, Iress may be required to provide the data subject with additional privacy information in respect to our processing of personal information to satisfy its regulatory obligations.
[7] When deciding whether a purpose is compatible with another, we may consider the nature of the personal information, if there is any relation between the two purposes, what the data subject would reasonably expect from the processing and any possible consequences the new processing might have on the data subject.
[8] For those processing in the UK, South Africa, and Australia, please refer to our Data Retention Policy for further guidance on our legal obligations to retain certain documents and guidance on setting retention periods.
[9] There may be grounds for refusing to comply with this type of request – for example, if the data remains necessary in relation to the purpose for which they were collected, if it needs to be retained for legal reasons or where the Iress has an overriding legitimate grounds for the processing.
[10] The approach to privacy-related assessments vary by region, but will be generally focused on identifying and considering mitigation of any privacy risks caused by the intended processing of personal information and demonstrating Iress’ approach to complying with relevant privacy legislation.
[11] Paragraph only applicable to Iress companies in the UK, EU, and South Africa.
[12] Case law in the United Kingdom has held that uploading personal information onto a webpage only constitutes a transfer to another country if the relevant webpage is actually accessed by a person located in that country. The process of merely uploading the data does not fall within the scope of the legislation.
[13] The European Commission has recognised Andorra, Argentina, Canada (commercial organisations concerning data subject to PIPEDA), Faroe Islands, Guernsey, Israel, Isle of Man, Japan (private sector organisations), Jersey, New Zealand, Republic of Korea, Switzerland, the UK, the United States of America (under the EU-US Data Privacy Framework and the UK extension), and Uruguay as providing adequate protection. The UK recognises the above countries, with the addition of all EEA and EFTA members and Gibraltar, as having adequate safeguards for the transfer of personal information.
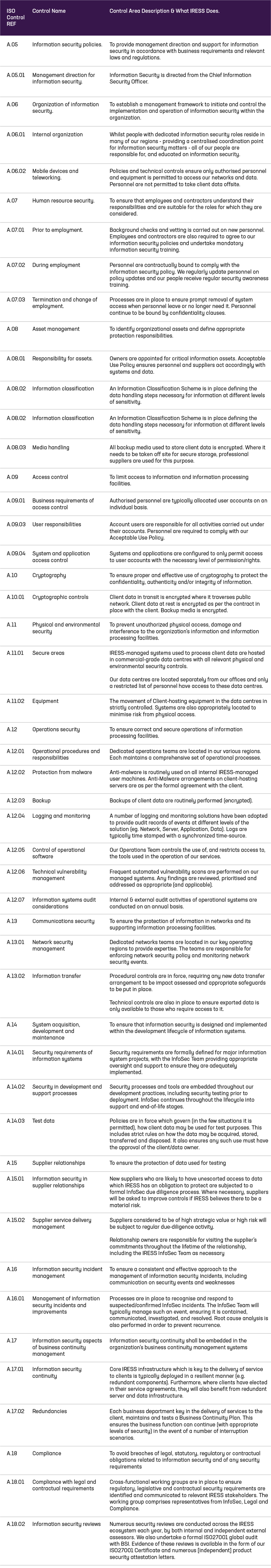
Information security summary and controls
Procedural & Technical Information Security Controls employed by IRESS
In our capacity as both a data processor and a controller, we adopt and maintain a formal framework of procedural and technical Information Security controls. Our control set is aligned to and independently certified to ISO27001, the international standard for information security management. The table below lists the ISO27001 information security controls we apply, together with a description of how we apply them. The effectiveness of these controls is reviewed on an ongoing basis through internal and external assessments as well as automated health check metrics.
Compliance contact
Iress has not appointed a Data Protection Officer in the UK and is not required to do so pursuant to Article 37 of the GDPR. The role and responsibilities that would typically be assumed by a Data Protection Officer are spread across our legal, information security, compliance and risk functions within Iress.
Queries in relation to Iress’ processing operations should be directed to Iress’ Compliance Officer who can be contacted at compliance@iress.com.
Any actual or suspected privacy breaches should be reported to our information security team who will manage the incident in accordance with its incident management procedure.
EU representative
If you are resident in the EU you may raise any issues or queries relating to our processing of your personal data with our EU representative (appointed pursuant to Article 27 of the GDPR).
Our EU representative is Iress SAS, a member of the Iress Group incorporated in France. Our EU representative can be contacted directly by emailing them at the following address: qhhr@iress.com
Iress is a technology company providing software to the financial services industry.

